In today's digital landscape, enterprises generate vast amounts of log data from various sources like servers, workstations, applications, and network devices. These logs are critical for monitoring system health, troubleshooting issues, and ensuring security. However, spotting anomalies in this vast amount of data can be extremely challenging and time-consuming. Traditional rule-based approaches are often inadequate due to their inability to adapt to evolving patterns and their reliance on predefined thresholds, which may lead to high false positive rates. This is where Machine Learning (ML) steps in, offering a more dynamic and adaptive solution for log anomaly detection.
Anomaly detection, in general, refers to the process of identifying patterns or instances in data that do not conform to expected behaviour or norms. These deviations, known as anomalies, outliers, or novelties, can represent significant events or abnormalities that warrant further investigation.
Logs are records of various activities, events, and system states captured by applications, servers, network devices, and other components of an IT infrastructure. Anomalies in log data may indicate potential security breaches, operational inefficiencies, or impending failures that require attention.
Using machine learning (ML) for anomaly detection in logs offers several merits compared to traditional rule-based methods. Here are some key advantages:
- Adaptability to Complex Patterns:
ML algorithms can learn complex patterns and relationships in log data that may not be captured by static rules.
- Scalability:
ML algorithms can efficiently process large volumes of log data, making them well-suited for scalable anomaly detection in high-throughput environments.
- Automation and Efficiency:
ML-based anomaly detection systems can automate the process of identifying and flagging anomalies in log data, reducing the need for manual intervention. This automation enhances operational efficiency and allows IT teams to focus their efforts on investigating and mitigating genuine security threats or operational issues.
- Granular Insights and Root Cause Analysis:
ML-based anomaly detection systems can provide granular insights into the nature and context of detected anomalies, facilitating root cause analysis and remediation efforts. By correlating anomalies across different log sources and contextualizing them with other relevant data, these systems help IT teams understand the underlying causes of abnormal behaviour and take appropriate action.
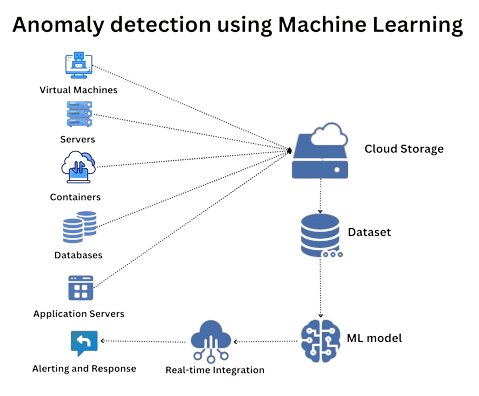
Implementation Steps
- Data Collection: Gather log data from various sources.
- Data Preprocessing: Clean the data, handle missing values, and normalize features.
- Feature Engineering: Extract relevant features from the log data.
- Model Selection: Choose the appropriate ML algorithm based on the nature of the logs and the anomalies.
- Training and Evaluation: Train the model on historical data and evaluate its performance.
- Deployment: Integrate the model into the monitoring system for real-time anomaly detection.
- Monitoring and Maintenance: Continuously monitor the model’s performance and retrain it with new data to maintain accuracy.
Business benefits
- Proactive Issue Detection:
ML algorithms can continuously monitor log data and detect anomalies in real-time. This proactive approach allows businesses to identify and address issues before they escalate into major problems, reducing downtime and preventing potential disruptions.
- Enhanced Security:
ML-based log anomaly detection can identify unusual patterns indicative of security breaches, such as unauthorized access attempts or data exfiltration activities. Early detection of such threats enables quicker response and mitigation, protecting the organization's sensitive data and infrastructure from cyber-attacks.
- Scalability:
As businesses grow, the volume of log data increases exponentially. ML solutions can scale to handle large datasets efficiently, ensuring that log monitoring and anomaly detection remain effective regardless of the data volume.
- Custom Intelligent Alerting:
ML-based solutions can offer customized intelligent alerting, tailoring notifications based on the severity and context of anomalies. This ensures that relevant stakeholders are alerted appropriately, reducing alert fatigue and ensuring that critical issues are prioritized and addressed promptly.
- Operational Insights:
Beyond detecting anomalies, ML can provide valuable insights into operational trends and patterns. Businesses can use these insights to optimize system performance, improve resource allocation, and enhance overall efficiency.
Machine Learning offers a powerful approach to log anomaly detection, providing dynamic, scalable, and accurate solutions for modern enterprises. By leveraging various ML techniques, organizations can enhance their monitoring capabilities, promptly detect and address anomalies, and maintain robust system health and security. As the digital landscape continues to evolve, ML-based log anomaly detection will become increasingly vital in ensuring the smooth operation of complex IT infrastructures.
