Service Principal Credential Expiry
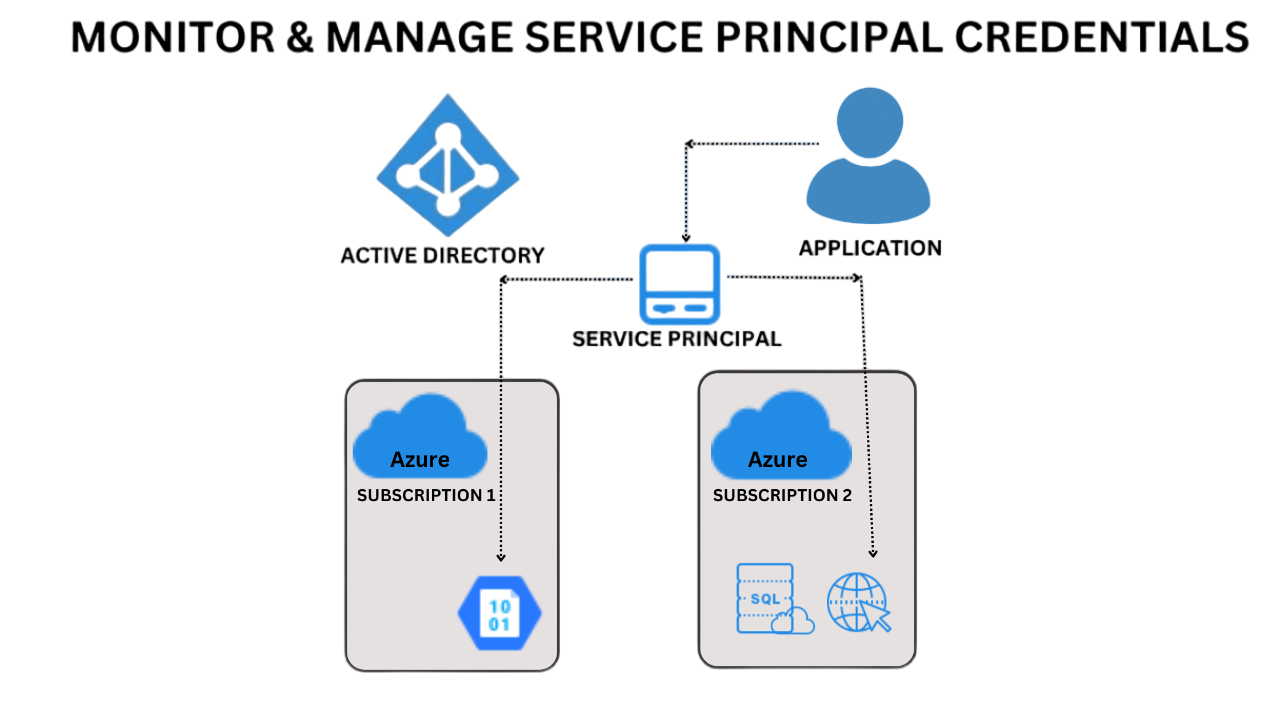
You can significantly enhance the security of your Azure environment and can protect your data and resources by using Service Principals. Hence it is important to manage service principal credential expiry. When service principal credentials expire, several issues can arise, affecting the functionality, security, and operations of applications and services within an Azure environment. Some of the key issues include:
- Access Management issues: As for an organisation they use various service principal for different applications and expiry of these service principals will force “Access Denied” errors and this results in the interruption of several operations and services.
- Security Risks: Outdated service principal credentials might still be kept in configurations, scripts, or code repositories, and so there occurs a security risk. This leads to the use of this credentials by third party users to gain unauthorized access to Azure resources.
- Data Loss: In some cases, expired service principal credentials lead to loss of data due to the denied access of resources or services.
- Authentication Issues: When trying to access Azure resources, authentication issues may arise due to expired service principal credentials. As a result, applications may not operate as intended and causes automated procedures to fail.
- Service Outage: Applications and services that depend on service principal credentials to access Azure resources may experience service disruptions or outages as a result of those credentials expiring. Both user experience and company operations may be impacted by this.
- Operational Challenges: Operational difficulties may arise while managing expired service principal credentials, such as the requirement to rapidly locate and update credentials across numerous apps and services. The IT and development teams may have more work as a result of this.
Methods for Handling Service Principal Credentials Expiry
In order to keep your Azure environment's safety measures solid, you must handle service principal credentials effectively. If credentials are not managed properly, there can be data loss, illegal access, and security threats. Thus, keeping your Azure environment's safety measures needs efficient credential management.
Methods for Handling Service Principal Credentials
From the above-mentioned points, we are aware of the risk factors that occurs due to service principal credential expiry. For this there are some pre-defined methods to effectively managing and handling service principal credentials expiry.
- Automated Credential Rotation
- Monitor Expiry Dates
- Scheduled Credential Updates
- Credential Management Tools
Other than applying these individual methods we can develop automated script to monitor the service principal credential expiry. We can use any scripting language, but I'll specifically recommend PowerShell because it has a large number of cmdlets for managing Azure resources. The script will monitor credential expiry, so that you can proactively address expiring credentials before they cause service interruptions. It also helps with the automated credential rotation. This will help with the risks that we mentioned earlier in the Service Principal Credential Expiry session.
- Access Management: Automating the monitoring of service principal credential expiry with a PowerShell script will help to prevent the “Access Denied” errors and results in the proper working of several operations and services.
- Security: Regularly monitoring service principal credential expiry helps ensure the security of Azure resources by updating or rotating credentials before expiry. This prevents unauthorized access.
- Prevention of Service Outage: By monitoring credential expiry, you can immediately address expiring credentials before they cause service interruptions. This helps maintain the availability and reliability of applications and services that rely on those credentials for authentication.
- Operational Efficiency: Using a PowerShell script to automate the monitoring of service principal credential expiration enhances operational efficiency. It makes adaptive credential management possible, which lowers the chance of human errors and eliminates the need for manual intervention.
Overall, keeping an eye on the expiration of service principal credentials via a PowerShell script is crucial to preserving Azure environments' operational effectiveness, security, and compliance. In the end, it contributes to a more robust and secure infrastructure by assisting enterprises in meeting regulatory requirements, proactively managing resource access, and reducing security threats.
Expired Credential Management
Usually, managing expired service principal credentials entails updating or renewing the credentials associated with the service principal. An overview of possible actions are shown below:
- Find the Expired Credentials: Finding out which service principal credentials have expired is the first step. You can review the logs for this or use the administrative tools provided by your identity management system.
- Generate new Credentials: Create new ones after identifying which ones are expired.
- Update Credentials: As soon as you get the new credentials update the system with this new credential like updating the configuration files.
Conclusion
In conclusion, service principal credential management is a crucial component of maintaining the security of your Azure system. You may successfully safeguard your Azure resources and reduce the risk of unauthorized access and data breaches by understanding the significance of service principles, putting best practices for credential management into practice, and taking practical measures to improve security.