Securing Your Azure Environment: A Guide to Service Principal Credential Management
Aswathy Sankar, June 2024
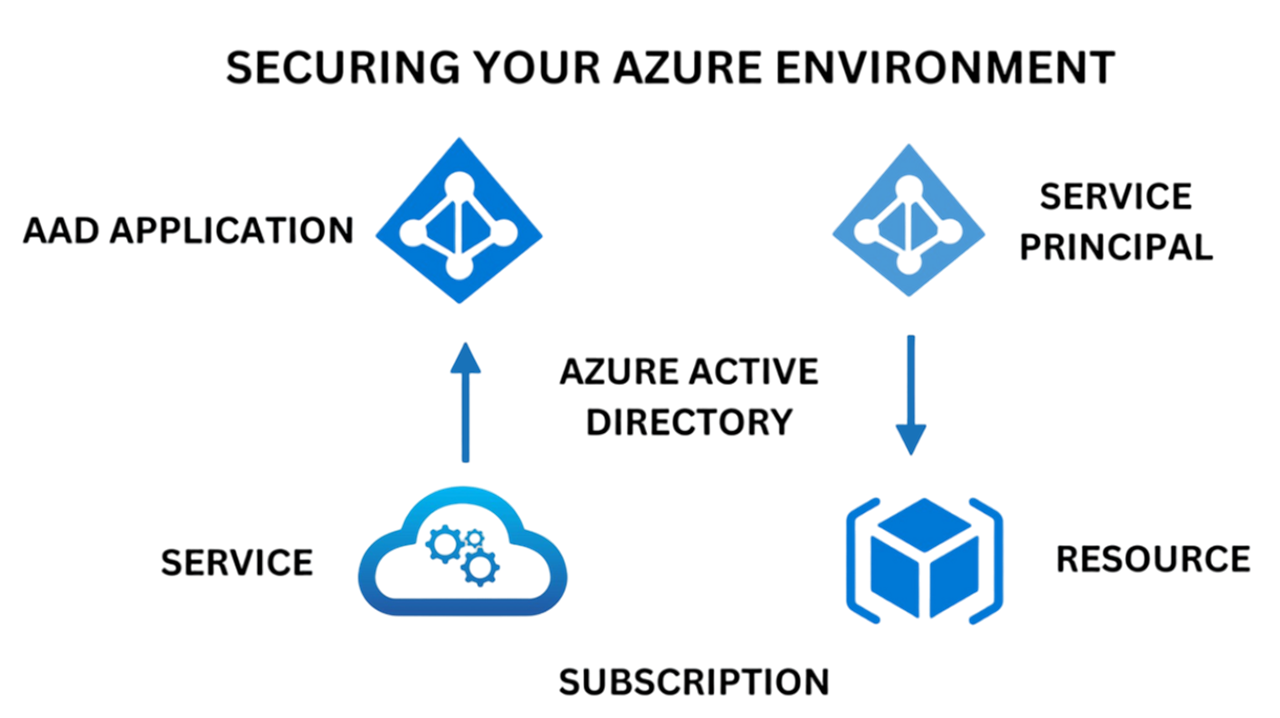
In the fast-paced world of Cloud Computing, every organization increasingly rely on cloud services like Microsoft Azure. So, ensuring the security of their cloud environments becomes important. Among the various security measures, managing service principal credentials is a critical aspect of maintaining a secure Azure environment. The purpose of this guide is to help you understand the importance of service principals, the risks associated with poor credential management, and practical steps you can take to improve your Azure security.
Understanding Service Principal
Before diving into credential management, let's clarify what service principals are in the context of Azure. In Azure, a service principal is a security identity used by applications, services, and automation tasks to access Azure resources securely. Consider it a "user identity" (service account) for programmatic non-human entities. A service principal enables automated access to resources without the need for human intervention, and so it can be used for a variety of Azure operations including deploying applications, managing services, and provisioning resources. And we can restrict service principal’s access by assigning them Azure RBAC roles.
Creating an Azure service principal can be done in several ways, such as through the Azure Portal, through Azure PowerShell, via the Rest API, or through Azure CLI. Azure does not grant permissions based on the creation of a service principal. The first thing you need to do is assign it some roles. These roles define the permissions and access of Service Principal over a subscription or resource.
Benefits of Service Principal
Importance of Service Principal Credential Management
In order to keep your Azure environment's safety measures solid, you must handle service principal credentials effectively. If credentials are not managed properly, there can be data loss, illegal access, and security threats. Thus, keeping your Azure environment's safety measures needs efficient credential management.
Methods for Handling Service Principal Credentials
As mentioned earlier, you must manage service principal credentials properly to maintain the security of your Azure environment and there are some traditional methods which help with service principal credential management
Conclusion
In conclusion, service principal credential management is a crucial component of maintaining the security of your Azure system. You may successfully safeguard your Azure resources and reduce the risk of unauthorized access and data breaches by understanding the significance of service principles, putting best practices for credential management into practice, and taking practical measures to improve security.